What is Network Virtualization?
In This Article, we'll What is Network Virtualization?, you need to understand Introduction to Network Virtualization if you new to Network Virtualization, so follow this Article: Network Virtualization
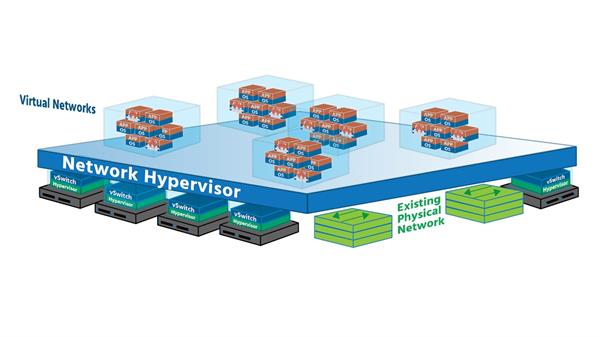
This hypervisor-based networking software (which will include security services as well) uses a controller to send network services to virtual switches and attaches the services to individual virtual machines (VMs) and containers. The result is a virtual network (The exact services will be determined by the policies already assigned to the VM/containers.). In this virtual network, whenever new VMs and containers are created, the appropriate policies are automatically applied to them, and when VMs and containers move, their networking and security move with them. (You'll sometimes hear VMs and containers referred to as workloads, so we'll use that term here to familiarize you with it.)
Creating a virtual network on top of a physical network is known as overlay networking. Imagine two devices (or endpoints) on an organization’s network – Finance Department Laptop and Sales Department Laptop, for example, both connected to physical network ports. (VMs and containers can be endpoints, too.) Both laptops are given a virtual network ID (VNID) and assigned to a virtual network. Virtual switches then connect Finance Department Laptop to Sales Department Laptop via virtual links (software representations of physical links) that form a tunnel across the network. Each virtual link corresponds to a path in the underlying physical network.
Network virtualization works just as well in the cloud and can be managed by using a Cloud Management Platform (CMP) such as VMware’s vRealize Automation or an open-source option such as Apache CloudStack and OpenStack. Hypervisor-based network virtualization can be set up and run using a Graphical User Interface (GUI) and a Command-Line Interface (CLI) or using Application Programming Interfaces (APIs).
Network virtualization provides administrators with tremendous flexibility. It can be used for networks as small as two connected devices, or as large as networks spanning multiple sites of major enterprises. In addition, it is flexible enough to work with any cloud or cluster (or pod if you’re using a new application framework like Kubernetes) while having different virtual networks that can be associated with different workloads. VMware’s NSX for vSphere (NSX-V) virtual network and security product works with ESXi (a Type 1 hypervisor - i.e., one that runs directly on the host’s hardware, independent of the host’s operation system), while their NSX-T Data Center works with ESXi and with KVM (a Type 2 hypervisor running within the host’s operating system).
Virtual networks are not to be confused with virtual local area networks – VLANs. A VLAN takes the ports of a physical switch and groups (or isolates) them to fit a specific purpose. An organization might have its Finance Department on the first floor, HR on the second and third, Production on the fourth, Sales on the fifth, and printers scattered around the building. On one physical switch, five VLANs could be created for these separate functions, each with its own broadcast domain.
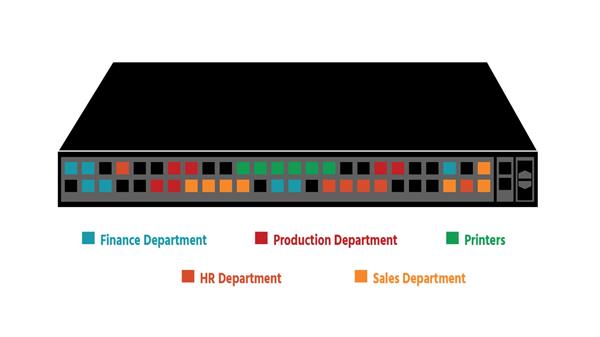
With network virtualization, on the other hand, network services beyond data transfer are also available – switching, routing, firewalling, and load balancing (Layer 3 to Layer 7 functions). The network in its entirety (Finance, HR, Production, Sales, and printers) can be recreated in software in seconds, and cloned or moved if needed; or snapshots representing the exact state of a network at a particular point in time can be created, saved, and used to recreate the network if required. Every networking and security service is virtualized (handled in software) and attached directly to individual workloads, reducing the need for physical configuration.