What is AWS IAM | AWS Identity and Access Management
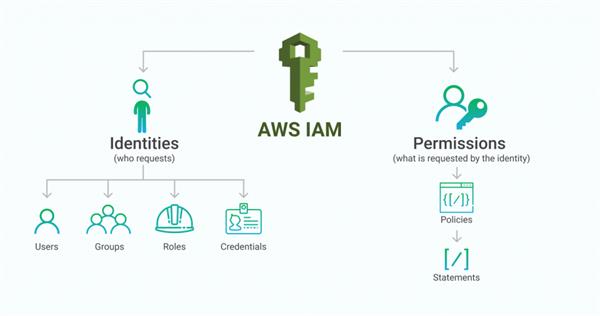
AWS IAM
AWS Identity and Access Management (IAM) is a web service that encourages you to safely control access to AWS resources. You use IAM to control who is validated (signed in) and authorized (has permissions) to utilize resources.

At the point when you initially make an AWS account, you start with a solitary sign-in character that has total access to all AWS services and resources in the record. This personality is known as the AWS account root client and is gotten to by marking in with the email address and secret key that you used to make the record. We unequivocally suggest that you don't utilize the root client for your ordinary errands, even the authoritative ones. Rather, stick to the best act of utilizing the root client just to make your first IAM client. At that point safely lock away the root client credentials and use them to perform just a couple of accounts and service the management tasks.
Policies
Features
Shared access to your AWS account
You can grant other people permission to administer and use resources in your AWS account without having to share your password or access key.
Granular permissions
You can give various consents to various individuals for various resources. For instance, you may permit a few clients complete access to Amazon Elastic Compute Cloud (Amazon EC2), Amazon Simple Storage Service (Amazon S3), Amazon DynamoDB, Amazon Redshift, and different AWS services. For different users, you can permit read-only access to simply some S3 buckets, or consent to manage only some EC2 instances, or to get to your charging data yet nothing else.
Secure access to AWS resources for applications that run on Amazon EC2
You can utilize IAM highlights to safely give accreditations to applications that sudden spike in demand for EC2 instances. These qualifications give authorizations to your application to get to different AWS resources. Models incorporate S3 buckets and DynamoDB tables.
Multi-factor authentication (MFA)
You can add two-factor verification to your record and to individual clients for additional security. With MFA you or your clients must give not just a secret word or access key to work with your record, yet additionally a code from a specially configured device.
Identity federation
You can allow users who already have passwords elsewhere—for example, in your corporate network or with an internet identity provider—to get temporary access to your AWS account.
Identity information for assurance
On the off chance that you use AWS CloudTrail, you get log records that incorporate data about the individuals who made solicitations for resources in your record. That data depends on IAM identities.
PCI DSS Compliance
IAM supports the processing, storage, and transmission of credit card data by a merchant or service supplier, and has been approved as being consistent with Payment Card Industry (PCI) Data Security Standard (DSS).
Eventually Consistent
IAM, in the same way as other AWS services, is eventually consistent. IAM accomplishes high accessibility by repeating data over different servers inside Amazon's databases on the world. On the off chance that a solicitation to change a few data is fruitful, the change is submitted and securely put away. In any case, the change must be reproduced across IAM, which can take some time. Such changes include creating or updating users, groups, roles, or policies. We suggest that you do exclude such IAM changes in the basic, high-availability code paths of your application. Rather, make IAM changes in a different statement or arrangement schedule that you run less as often as possible. Likewise, make sure to check that the progressions have been propagated before production workflows depend upon them.
Free to use
AWS Identity and Access Management (IAM) and AWS Security Token Service (AWS STS) are features of your AWS account offered at no additional charge. You are charged only when you access other AWS services using your IAM users or AWS STS temporary security credentials.
Use cases
Fine-grained access control to AWS resources
IAM empowers your clients to control access to AWS service APIs and to explicit resources. IAM likewise empowers you to include explicit conditions, for example, time of day to control how a client can utilize AWS, their starting IP address, regardless of whether they are utilizing SSL, or whether they have verified with a multi-factor authentication device.
Multi-factor authentication for highly privileged users
Protect your AWS environment by using AWS MFA, a security feature available at no extra cost that augments user name and password credentials. MFA requires users to prove physical possession of a hardware MFA token or MFA-enabled mobile device by providing a valid MFA code.
Analyze access
IAM encourages you to analyze access over your AWS condition. Your security groups and chairmen can rapidly approve that your strategies just give the planned open and cross-account access to your resources. You can likewise effectively recognize and refine your arrangements to permit access to just the services being utilized. This causes you to all the more likely cling to the guideline of least privilege.
Integrate with your corporate directory
IAM can be used to grant your employees and applications federated access to the AWS Management Console and AWS service APIs, using your existing identity systems such as Microsoft Active Directory. You can use any identity management solution that supports SAML 2.0, or feel free to use one of their federation samples (AWS Console SSO or API federation).