What is AWS Bucket?
What is AWS Bucket?
An AWS S3 bucket is an open distributed storage resource accessible in Amazon Web Services' (AWS) Simple Storage Service (S3), an item stockpiling offering. Amazon S3 buckets, which are like record organizers, store objects, which comprise of information and its clear metadata.
To transfer your information (photographs, recordings, reports, and so on.) to Amazon S3, you should initially make an S3 bucket in one of the AWS regions. You would then be able to transfer any number of articles to the bucket. As far as usage, buckets and articles are resources, and Amazon S3 gives APIs to you to oversee them. An Amazon S3 bucket name is all-inclusive special, and the namespace is shared by all AWS accounts. This implies after a bucket is made, the name of that bucket can't be utilized by another AWS account in any AWS Region until the bucket is erased. You ought not to rely upon explicit bucket naming shows for accessibility or security confirmation purposes.
Amazon S3 makes buckets in a Region you indicate. To enhance idleness, limit expenses, or address administrative necessities, pick any AWS Region that is geologically near you.
Making a bucket
Amazon S3 gives APIs to making and overseeing buckets. As a matter of course, you can make up to 100 buckets in every one of your AWS accounts. On the off chance that you need more buckets, you can expand your record bucket cut-off to a limit of 1,000 buckets by presenting a help limit increment. You can store any number of items in a bucket.
At the point when you make a bucket, you give a name and the AWS Region where you need to make the bucket. For data about naming buckets, see Rules for bucket naming. You can utilize any of the techniques recorded underneath to make a bucket.
Amazon S3 console
You can create a bucket in the Amazon S3 console.
REST API
Making a bucket utilizing the REST API can be unwieldy since it expects you to compose code to verify your requests. We suggest that you utilize the AWS Management Console or AWS SDKs.
AWS SDK
At the point when you utilize the AWS SDKs to make a bucket, you initially make a customer and afterward utilize the customer to send a request to make a bucket. In the event that you don't indicate a Region when you make a customer or a bucket, Amazon S3 utilizes US East (N. Virginia), the default Region. You can likewise determine a particular Region.
As a best practice, you ought to make your customer and bucket in a similar Region. In the event that your Region launched after March 20, 2019, your customer and bucket must be in a similar Region. In any case, you can utilize a customer in the US East (N. Virginia) Region to make a bucket in any Region that propelled before March 20, 2019.
Making a customer
At the point when you make the customer, you ought to indicate an AWS Region, to make the customer in. In the event that you don't indicate a Region, Amazon S3 makes the customer in US East (N. Virginia) as a matter of course Region. To make a customer get to a double stack endpoint, you should indicate an AWS Region.
At the point when you make a customer, the Region maps to the Region-explicit endpoint. The customer utilizes this endpoint to speak with Amazon S3:
Making a bucket
In the event that you don't determine a Region when you make a bucket, Amazon S3 makes the bucket in the US East (N. Virginia) Region. Hence, in the event that you need to make a bucket in a particular Region, you should indicate the Region when you make the bucket.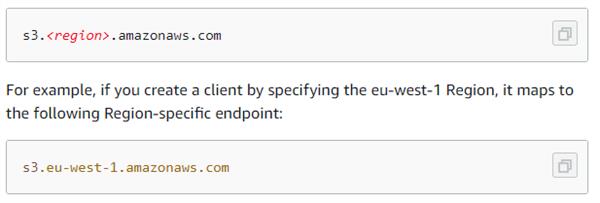
Buckets made after September 30, 2020, will support just virtual facilitated style demands. Path style requests will keep on being supported for buckets made at the very latest this date.
About permissions:
You can utilize your AWS account root certifications to make a bucket and play out some other Amazon S3 activity. Be that as it may, AWS suggests not utilizing the root accreditations of your AWS record to make demands, for example, to make a bucket. Rather, make an IAM client, and award that client full access (clients as a matter, of course, have no authorizations). We refer to these clients as director clients. You can utilize the chairman client certifications, rather than the root qualifications of your record, to cooperate with AWS and perform assignments, for example, make a bucket, make clients, and award them consents.
The AWS account makes a resource and claims that resource. For instance, in the event that you make an IAM client in your AWS record and award the client consent to make a bucket, the client can make a bucket. In any case, the client doesn't possess the bucket; the AWS record to which the client has a place claims the bucket. The client will require extra authorization from the resource proprietor to play out some other bucket tasks.
Managing public access to buckets
Public access is allowed to buckets and objects through access control lists (ACLs), bucket approaches, or both. To assist you with managing public access to Amazon S3 resource, Amazon S3 gives block public access settings. Amazon S3 block public access settings can override ACLs and bucket arrangements so you can uphold uniform cutoff points on public access to these resources. You can apply block public access settings to singular buckets or to all buckets in your record.
To help guarantee that the entirety of your Amazon S3 buckets and objects have their public access blocked, we suggest that you turn on every one of the four settings for blocking public access for your record. These settings block public access for all current and future buckets.
Before applying these settings, confirm that your applications will work accurately without public access. In the event that you require some degree of public access to your buckets or objects, for instance, to have a static site as portrayed at Hosting a static site on Amazon S3, you can modify the individual settings to suit your capacity use cases.
Accessing a bucket
You can access your bucket utilizing the Amazon S3 comfort. Utilizing the console UI, you can perform practically all bucket tasks without composing any code.
On the off chance that you access a bucket automatically, note that Amazon S3 underpins RESTful engineering in which your buckets and objects are resources, each with a resource URI that exceptionally recognizes the resource.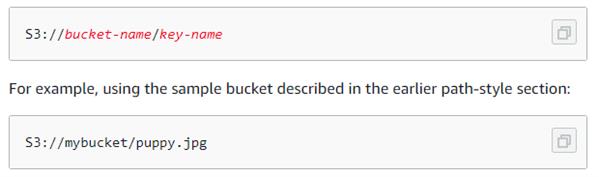
Amazon S3 underpins both virtual-facilitated style and way style URLs to access a bucket. Since buckets can be accessed utilizing way style and virtual-facilitated style URLs, we suggest that you make buckets with DNS-consistent bucket names.
Note
Virtual hosted style and path-style requests use the S3 dot Region endpoint structure (s3.Region), for example, https://my-bucket.s3.us-west-2.amazonaws.com. However, some older Amazon S3 Regions also support S3 dash Region endpoints s3-Region, for example, https://my-bucket.s3-us-west-2.amazonaws.com. If your bucket is in one of these regions, you might see s3-Region endpoints in your server access logs or CloudTrail logs. We recommend that you do not use this endpoint structure in your requests.
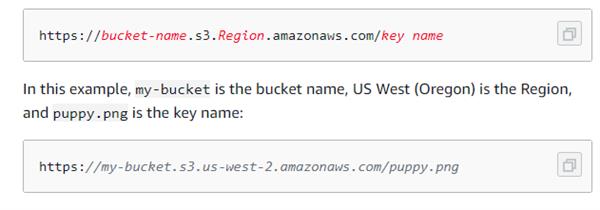
Virtual hosted style access
In a virtual-facilitated style demand, the bucket name is a piece of the domain name in the URL. Amazon S3 virtual hosted style URLs follow the arrangement demonstrated as follows.
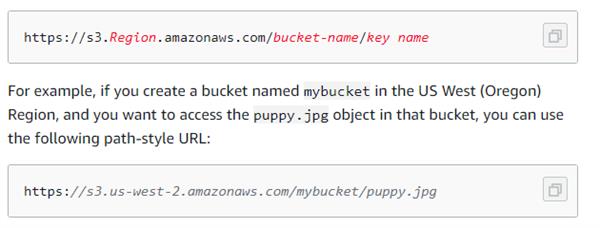
 Path style access
Path style access
In Amazon S3, Path style URLs follow the format shown below.
Important
Buckets made after September 30, 2020, will bolster just virtual facilitated style demands. Way style solicitations will keep on being upheld for buckets made at the very latest this date.
Accessing an S3 bucket over IPv6
Amazon S3 has a lot of double-stack endpoints, which supports requests to S3 buckets over both Internet Protocol form 6 (IPv6) and 4 (IPv4).
One can get to a bucket through an S3 access point. An S3 access point just helps virtual-host- style addressing to address a bucket through an access point. Additionally, we can also access it directly.
Note
On the off chance that your access point name incorporates dash (- ) characters, remember the dash for the URL and add another dash before the record ID. For instance, to utilize an access point named money docs possessed by account 123456789012 in Region us-west-2, the proper URL would be https://fund docs-123456789012.s3-accesspoint.us-west-2.amazonaws.com.
Access by HTTP is not supported in S3, just secure access by HTTPS.
Some AWS administrations require indicating an Amazon S3 bucket utilizing S3://bucket. The right arrangement is demonstrated as follows. Know that when utilizing this configuration, the bucket name does exclude the region.
Bucket arrangement choices
Amazon S3 underpins different choices for you to arrange your bucket. For instance, you can arrange your bucket for site facilitating, add design to deal with the lifecycle of items in the bucket, and design the bucket to log all entrance to the bucket. Amazon S3 underpins subresources for you to store and deal with the bucket design data. You can utilize the Amazon S3 API to make and deal with these sub-resources. In any case, you can likewise utilize the comfort or the AWS SDKs.
Note: There are additionally object-level arrangements. For instance, you can arrange object-level authorizations by designing an access control list (ACL) explicit to that object.
These are referred to as sub-resources in light of the fact that they exist with regards to a particular bucket or article.
As a pre-requisite one can also read about AWS S3, Regions, and REST API to get a better understanding of AWS Bucket. If you have any doubt, do write to us in the comment section. Keep reading and Stay healthy.