Cloud Storage Security issues
Cloud computing is a technology of sharing resources on the internet. These platforms offer efficient access to a company’s high-performance computing and storage infrastructure. Data security becomes a major problem in the cloud. Data security and data privacy are the two main aspects of cloud information technology. Data privacy and security protection are the most significant aspect of the enhancement and development of cloud computing in the field of business and government sectors.in this paper, we will discuss the security issues of cloud and security methods used for data storage on the cloud.
INTRODUCTION
Cloud computing is the next generation paradigm in information technology .it is an auspicious way for data storage and data transmission. The cloud computing environment provides a way to access both resources and applications on-demand through the internet. Today many organizations are moving into the cloud because they provide the facility to store data on the cloud and we can access it anytime and from anywhere. Cloud computing can differentiate into two subsections as the cloud and the user.
In most cases, the individual user connected to the cloud environment through the internet. Loud computing has normal functions such as the user requests to the cloud and the cloud response to the user.
Security and privacy are major concerns on cloud computing i.e. confidentiality, integrity, and availability of data. Different types of tolls have been generating to accomplish these concerns, such as access control, authentication, audition, digital signature.
SECURITY SERVICES
To address the above concerns and increase the adoption of cloud storage it’s good to design virtual private storage based on recently developed cryptography techniques.
Confidentiality: The cloud storage provider does not learn or store any information about the customer.
Integrity: Any type of modification of customer data by the cloud storage provider can be detected by the customer.
Availability: Cloud data is accessible from any machine and any time.
Reliability: Customer data stored on the cloud is reliably backed up.
Data sharing: Cloud computing provides the facility to share the data with trusted parties.
CLOUD STORAGE
Cloud storage is the model of computer data storage in which the digital data stored in logical pools. Cloud storage providers are responsible for keeping the data available and accessible.
Four types of cloud storage are there.
Personal cloud storage:
It’s also known as mobile cloud storage.in which individual’s data stored in the cloud. These types of cloud storage come in two formats: on-premise and externally hosted.
Public Cloud Storage:
This type of storage requires little administrative controls and can online be accessed by anyone. You don’t need a rigid integration with your business need.
The cloud storage provider fully manages the enterprise’s public cloud storage.
Private Cloud Storage:
Private cloud storage also called internal cloud storage, it’s a service delivery model for storage.
Private cloud storage help resolve the possibility for safety and performance concern while offering many of the benefits of cloud storage such as quantitative, reliability, rapid development.
Hybrid Cloud Storage:
It is a mixture of private and public clouds by allowing data and applications to be shared between them.
Although the private and public segments of the hybrid cloud are bound together, to remain unique entities.
CLOUD SECURITY AND PRIVACY ISSUES
Once the data upload into the cloud then the user loses control over the data and data accessed by the attackers.
There are many cloud storage security issues as they provide hardware and services over the internet.
Network security
Data were taken from enterprise in Saas and stored by Saas providers. To prevent the leakage of the confidential information data over the internet must secure.
Data Confidentiality
Confidentiality is a major issue in cloud computing. Confidentiality means accessing the data only by authorized users. it means to keep the data secure on the cloud.
Encryption algorithms used to secure data from malicious users. Encryption used to convert the original data in a coded form known as cipher text.
Encryption algorithms have some limitations, if user wants to read, search and update the records of file then we need to decrypt the entire file or records.
Data Integrity
Integrity means to make sure data has not been changed by unauthorized users. Cloud computing supports the features of resource sharing, it creates the problem of corruption of data by unauthorized access[7]. So, It’s another serious problem faced by cloud computing.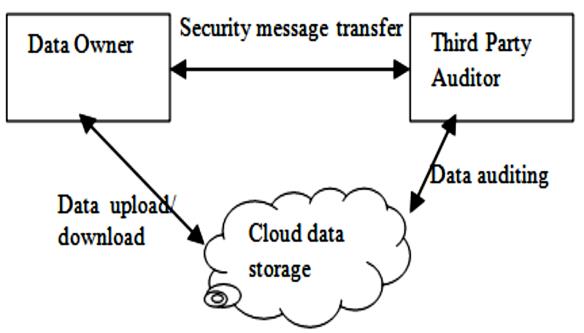
Remote Data integrity checking protocol use on cloud to remove the data integrity issue from cloud .
Availability
It refers to make sure resources will be available and accessible to the authorized users on request. This service of cloud computing provide the benefit to access the resources at anytime and anywhere.
In an earlier stage of cloud computing data availability was major issue due to lack of reliability and certain infrastructure.
DOS Attack
DOS refers to Denial of service attack. In which attacker sends excessive messages asking the network to authenticate requests that have return invalid addresses[8]. Cloud also provides the services to users that have malicious purposes.
It Origin the following problems:
- Ineffectual service
- Unreachable services
- Network traffic
- Interference in communication
VM Attacks
Cloud computing architecture divided into different section Front and Back-end. Client and users are on front-end and cloud provides are on back-end. The front-end need to access the cloud architecture and on back-end includes different virtual machines, data storage system and servers. Cloud developers required to take care of cloud attacks when implementation done.
Virtual machine emulators come in two forms: Hardware bound and pure software.
Malicious insiders
Most information loss happens inside association through human mistakes. Inside attackers previous or present employees , contractual workers who has the access to get the organization information and harm that data.
Permanent data loss
Information loss can a permanent harmful to the business. It’s the cloud supplier duty to make composition for human mistake and to construct strong physical farms.
Shared technology and resources
Cloud suppliers allow clients to share resources and information on cloud. In this situation , malicious users can inject a malicious code in cloud data and threats targeting the client system and one client performance impact on other clients.
Hacked interfaces and APIs
APIs are the backbone of cloud computing and in distributed computing it works as an integration amongst clients. For security of cloud its necessary to secure the APIs . To work with cloud merchants to construct data streams that don’t open APIs.
System vulnerabilities
Cloud computing system contain system vulnerabilities , especially in complex infrastructures and third-party platforms.if any vulnerability becomes known with third-party then this vulnerability can easily used against organization.
SOLUTIONS TO SECURITY ISSUES
Many of the risk and issues can protected through the use of dedicated data protection services. Cloud protection solutions protect the data from data loss and security threats.
Security policies plan:
Cloud service providers should write security policies plan to ensure security of data, if the providers do not have security service plan then the cloud is not safe. Organizations can organize the data security development programs.
Multifarious Authentication:
Cloud provides can give the multi-factor authentication. If any unauthorized user wants to use the data then he/ she needs to process through multiple login.
For example: if malicious user try to access the data through password and the password is wrong then wrong password should sent to the owner mobile phone so that he/ she can authenticate the login of data.
Access to the data
Data must use and seen by the administrator only, not by the user. This access will give security of data and enhance the accuracy of data .
Appropriate cloud model for organization
Cloud model for business will be private cloud. It is costly but more secure than public cloud, because private clouds are only used by one organization that’s why security level will be higher than public cloud.
Backups encryption
Backups of cloud data must encrypt to keep up the security level. If data stored on cloud encrypted but backups are not encrypted then it does not make sense to store the data on cloud in an encrypted form. Data should secure over its entire life cycle.
Secure data devastation
Destruction of data should secure , if data wipe out is not secure then the risk of data leakage can increase and anyone can use the data.
Encryption scheme testing:
If the encryption schemes designed and tested by the experienced persons then security of data can trustworthy.security questions will designed and conducted to keep up security of data on cloud.
CONCLUSION
Cloud computing is a technology that based on internet and it is a less expensive technology to share the resources over internet. Despite of numerous advantages there are many issues in cloud computing environment about security of data and data storage over the internet.These approaches have to more efficient and effective, so that cloud service consumers should accept these services.business organization expects a strong trustworthiness between owner and service provider.
In this review paper I tried to find out the data storage security issues in cloud environment .This will provide the help to cloud users to understand the data security level of cloud whether it is safe to store the data on cloud and on what security levels.