What is AWS ECR?
What is AWS ECR?
Amazon Elastic Container Registry (Amazon ECR) is an overseen AWS Docker vault administration that is secure, versatile, and dependable. Amazon ECR bolsters private Docker archives with asset-based authorizations utilizing AWS IAM so explicit clients or Amazon EC2 cases can get to stores and pictures. Engineers can utilize the Docker CLI to push, pull, and oversee pictures.

The AWS holder administration group keeps up an open guide on GitHub. It contains data about what the groups are taking a shot at and permits all AWS clients the capacity to give direct criticism. Amazon Elastic Container Registry (ECR) is a completely overseen Docker compartment vault that makes it simple for engineers to store, oversee, and send Docker holder pictures.
Amazon ECR is coordinated with Amazon Elastic Container Service (ECS), improving your improvement to the creative work process. Amazon ECR dispenses with the need to work your own compartment stores or stress over scaling the hidden foundation. Amazon ECR has your pictures in profoundly accessible and versatile engineering, permitting you to dependably send compartments for your applications. Mix with AWS Identity and Access Management (IAM) gives asset level control of every storehouse. With Amazon ECR, there are no forthright charges or duties. You pay just for the measure of information you store in your vaults and information moved to the Internet.
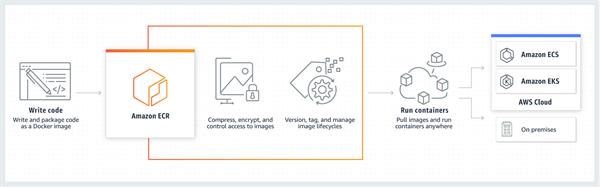
Parts of Amazon ECR
Amazon ECR contains the accompanying parts:
Registry
An Amazon ECR registry is given to each AWS account; you can make picture storehouses in your vault and store pictures in them.
Authorization token
Your Docker customer must validate to the Amazon ECR registry as an AWS client before it can push and pull pictures.
Repository
An Amazon ECR picture archive contains your Docker or Open Container Initiative (OCI) pictures. For more data, see Amazon ECR Repositories.
Repository policy
You can control access to your archives and the pictures inside them with storehouse approaches.
Image
You can push and pull holder pictures to your storehouses. You can utilize these pictures locally on your advancement framework, or you can utilize them in Amazon ECS task definitions and Amazon EKS unit particulars.
Amazon ECR Registries
Amazon ECR libraries have your holder pictures in exceptionally accessible and adaptable design, permitting you to convey compartments dependably for your applications. You can utilize your vault to oversee picture storehouses comprising of Docker and Open Container Initiative (OCI) pictures. Each AWS account is given a solitary (default) Amazon ECR vault.
Registry Concepts
The URL for your default library is https://aws_account_id.dkr.ecr.region.amazonaws.com.
Naturally, your record has perused and composed access to the stores in your default library. Be that as it may, IAM clients expect authorization to make calls to the Amazon ECR APIs and to push or pull pictures from your archives. Amazon ECR gives a few oversaw approaches to control client access at different levels. For more data, see Amazon Elastic Container Registry Identity-Based Policy Examples.
You should confirm your Docker customer to a vault with the goal that you can utilize the docker push and docker pull orders to push and pull pictures to and from the stores in that library. For more data, see Registry Authentication.
Vaults can be controlled with both IAM client get to arrangements and storehouse approaches. For more data about archive strategies, see Amazon ECR Repository Policies.
Registry Authentication
You can utilize the AWS Management Console, the AWS CLI, or the AWS SDKs to make and oversee vaults. You can likewise utilize those techniques to play out certain activities on pictures, for example, posting or erasing them. These customers utilize standard AWS verification techniques. Albeit in fact, you can utilize the Amazon ECR API to push and pull pictures, you are significantly more liable to utilize the Docker CLI or a language-explicit Docker library.
The Docker CLI doesn't bolster local IAM confirmation strategies. Extra advances must be taken with the goal that Amazon ECR can validate and approve Docker push and pull demands.
The accompanying registry authentication strategies are accessible.
Utilizing the Amazon ECR Credential Helper
Amazon ECR gives a Docker accreditation aide which makes it simpler to store and use Docker qualifications when pushing and pulling pictures to Amazon ECR. For establishment and design steps, see Amazon ECR Docker Credential Helper.
Utilizing an Authorization Token
An approval token's authorization scope coordinates that of the IAM chief used to recover the confirmation token. A confirmation token is utilized to get to any Amazon ECR library that your IAM chief approaches and is legitimate for 12 hours. To get an approval token, you should utilize the GetAuthorizationToken API activity to recover a base64-encoded approval token containing the username AWS and an encoded secret key. The AWS CLI get-login-secret phrase order disentangles this by recovering and unraveling the approval token which you would then be able to pipe into a docker login order to verify.
Amazon ECR Repositories
Amazon Elastic Container Registry (Amazon ECR) gives API tasks to make, screen, and erase picture repositories and set consents that control who can get to them. You can play out similar activities in the Repositories area of the Amazon ECR comfort. Amazon ECR likewise incorporates with the Docker CLI permitting you to push and pull pictures from your advancement surroundings to your repositories.
Repository Concepts
Of course, your record has perused and composed access to the repositories in your default registry (aws_account_id.dkr.ecr.region.amazonaws.com). Be that as it may, IAM clients expect authorization to make calls to the Amazon ECR APIs and to push or pull pictures from your repositories. Amazon ECR gives a few oversaw arrangements to control client access at different levels; for more data, see Amazon Elastic Container Registry Identity-Based Policy Examples.
Repositories can be controlled with both IAM client get to strategies and repository approaches. For more data, see Amazon ECR Repository Policies.
Repository names can bolster namespaces, which you can use to assemble comparative repositories. For instance, if there are a few groups utilizing a similar registry, Team A could utilize the group a namespace while Team B utilizes the group b namespace. Each group could have its own picture called web-application, but since they are each introduced with the group namespace, the two pictures can be utilized all the while without obstruction. Group A's picture would be called the group a/web-application, while Team B's picture would be called group b/web-application.
Pictures
Amazon Elastic Container Registry (Amazon ECR) stores Docker and Open Container Initiative (OCI) pictures in picture repositories. You can utilize the Docker CLI to push and pull pictures from your repositories.
Amazon ECR Monitoring
You can screen your Amazon ECR API use with Amazon CloudWatch, which gathers and procedures crude information from Amazon ECR into discernible, close to continuous measurements. These measurements are recorded for a time of about fourteen days with the goal that you can get to authentic data and increase point of view on your API use. Amazon ECR metric information is consequently sent to CloudWatch in one-minute time spans. For more data about CloudWatch, see the Amazon CloudWatch User Guide.
Amazon ECR gives measurements dependent on your API use for approval, picture push, and picture pull activities.
Checking is a significant piece of keeping up the dependability, accessibility, and execution of Amazon ECR and your AWS arrangements. We suggest that you gather observing information from the assets that make up your AWS arrangement with the goal that you can all the more effectively investigate a multi-point disappointment in the event that one happens. Before you begin checking Amazon ECR, be that as it may, you ought to make an observing arrangement that incorporates answers to the accompanying inquiries:
What are your observing objectives?
What assets will you screen?
How regularly will you screen these assets?
What observing devices will you use?
Who will play out the observing errands?
Who ought to be told when something turns out badly?
The subsequent stage is to set up a standard for typical Amazon ECR execution in your condition by estimating execution at different occasions and under various burden conditions. As you screen, Amazon ECR, store chronicled observing information so you can contrast it and new execution information, recognize typical execution examples and execution peculiarities and devise techniques to address issues.
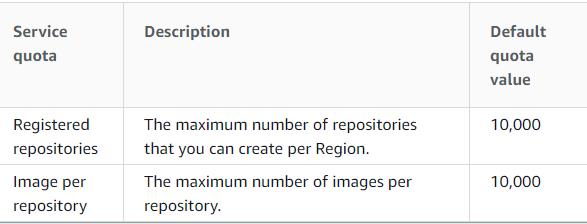
Amazon ECR administration amounts
The accompanying table gives the default administration portions to Amazon Elastic Container Registry (Amazon ECR).
The accompanying table gives the default rate standards to every one of the Amazon ECR API activities engaged with the picture push and picture pull activities.
The accompanying table gives different amounts to Amazon ECR and Docker pictures that can't be changed.
Note: The layer part data referenced in the accompanying table is just pertinent on the off chance that you are calling the Amazon ECR API activities straightforwardly to start multipart transfers for picture push tasks. This is an uncommon activity. We suggest that you utilize the Docker CLI to pull, tag, and push pictures.
Dealing with your Amazon ECR administration quantities in the AWS Management Console
Amazon ECR has incorporated with Service Quotas, an AWS administration that empowers you to see and deal with your quantities from a focal area.
Administration Quotas makes it simple to look into the estimation of all Amazon ECR administration amounts.
To see Amazon ECR administration amounts (AWS Management Console)
Open the Service Quotas support at https://console.aws.amazon.com/servicequotas/.
In the route sheet, pick AWS administrations.
From the AWS administration list, scan for and select Amazon Elastic Container Registry (Amazon ECR).
In the Service quantities show, you can see the administration portion name, applied worth (on the off chance that it is accessible), AWS default amount, and whether they share esteem is flexible.
To see extra data about an assistance standard, for example, the depiction, pick the portion name.
Making a CloudWatch caution to screen API use measurements
Amazon ECR gives CloudWatch use measurements that compare to the AWS administration portions for every one of the APIs engaged with the registry verification, picture push, and picture pull activities. In the Service Quotas support, you can imagine your use on a chart and design cautions that alert you when your utilization moves toward a helping share.