What is AWS HSM | AWS CloudHSM
AWS CloudHSM
AWS CloudHSM is a cryptographic service for making and keeping up equipment security modules (HSMs) in your AWS condition. HSMs are computing devices that procedure cryptographic activities and give the secure capacity to cryptographic keys. You can utilize AWS CloudHSM to offload SSL/TLS preparing for web servers, ensure private keys connected to an issuing certificate authority (CA), or empower Transparent Data Encryption (TDE) for Oracle databases.
When you use an HSM from AWS CloudHSM, you can perform a variety of cryptographic tasks:
- Generate, store, import, export, and manage cryptographic keys, including symmetric keys and asymmetric key pairs.
- Use symmetric and asymmetric algorithms to encrypt and decrypt data.
- Use cryptographic hash functions to compute message digests and hash-based message authentication codes (HMACs).
- Cryptographically sign data (including code signing) and verify signatures.
- Generate cryptographically secure random data.
AWS CloudHSM composes HSMs in clusters, which are naturally synchronized collections of HSMs inside a given Availability Zone (AZ). By adding more HSMs to a group and circulating clusters across AZs, you can stack balance the cryptographic tasks being performed inside your cloud condition and give excess and high accessibility if there should be an occurrence of AZ failure. Moreover, AWS CloudHSM intermittently creates and stores backups of your bunches, making CloudHSM data recuperation secure and basic.
Benefits
Generate and use encryption keys on FIPS 140-2 level 3 validated HSMs
AWS CloudHSM empowers you to create and utilize your encryption keys on a FIPS 140-2 Level 3 approved equipment. CloudHSM secures your keys with select, single-occupant access to alter safe HSM cases in your own Amazon Virtual Private Cloud (VPC).
Deploy secure, compliant workloads
Using HSMs as the foundation of trust encourages you to show consistency with security, protection, and hostile to alter guidelines, for example, HIPAA, FedRAMP, and PCI. AWS CloudHSM empowers you to construct secure, agreeable outstanding tasks at hand with high unwavering quality and low idleness, utilizing HSM occasions in the AWS cloud.
Use an open HSM built on industry standards
You can utilize AWS CloudHSM to incorporate with custom applications utilizing industry-standard APIs, for example, PKCS#11, Java Cryptography Extensions (JCE), and Microsoft CryptoNG (CNG) libraries. You can likewise move your keys to other business HSM answers to make it simple for you to relocate keys on or off of AWS.
Keep control of your encryption keys
AWS CloudHSM gives you access to your HSMs over a safe channel to make clients and set HSM arrangements. The encryption keys that you produce and use with CloudHSM are available just by the HSM clients that you determine. AWS has zero ability to see or access to your encryption keys.
Easy to manage and scale
AWS CloudHSM mechanizes tedious HSM authoritative errands for you, for example, equipment provisioning, programming fixing, high accessibility, and reinforcements. You can scale your HSM limit rapidly by including and expelling HSMs from your cluster on-request. AWS CloudHSM naturally load adjusts demands and safely copies keys put away in any HSM to the entirety of the different HSMs in the cluster.
Control AWS KMS keys
You can arrange AWS Key Management Service (KMS) to utilize your AWS CloudHSM cluster as a custom key store as opposed to the default KMS key store. With a KMS custom key store, you profit by the integration among KMS and AWS services that scramble data while holding control of the HSMs that secure your KMS ace keys. KMS custom key store gives you the best of the two universes, consolidating single-occupant HSMs under your influence without hardly lifting a finger of utilization and reconciliation of AWS KMS.
Key Features
Scalable HSM capacity
AWS CloudHSM makes it easy to scale your HSM capacity. You can add and remove HSMs on-demand using the AWS Management Console and AWS API.
Open solution
AWS CloudHSM is an open solution that eliminates vendor lock-in. With CloudHSM, you can transfer your keys to other commercial HSM solutions to make it easy for you to migrate keys on or off of the AWS Cloud.
Industry-standard APIs
AWS CloudHSM offers integration with custom applications via industry-standard APIs and supports multiple programming languages, including PKCS#11, Java Cryptography Extensions (JCE), and Microsoft CryptoNG (CNG) libraries.
Secure authentication
AWS CloudHSM supports quorum authentication for critical administrative and key management functions. CloudHSM also supports multi-factor authentication (MFA) using the tokens you provide.
AWS-managed infrastructure
AWS CloudHSM is a managed service that automates time-consuming administrative tasks, such as hardware provisioning, software patching, high availability, and backups.
How it works
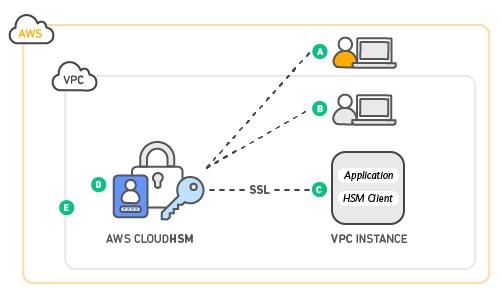
AWS CloudHSM runs in your own Amazon Virtual Private Cloud (VPC), empowering you to effortlessly utilize your HSMs with applications running on your Amazon EC2 instances. With CloudHSM, you can utilize standard VPC security controls to oversee access to your HSMs. Your applications associate with your HSMs utilizing commonly verified SSL channels built up by your HSM customer programming. Since your HSMs are situated in Amazon datacenters close to your EC2 instances, you can lessen the network inactivity between your applications and HSMs versus an on-premises HSM.
- AWS manages the hardware security module (HSM) appliance but does not have access to your keys
- You control and manage your own keys
- Application performance improves (due to close proximity with AWS workloads)
- Secure key storage in tamper-resistant hardware available in multiple Availability Zones (AZs)
- Your HSMs are in your Virtual Private Cloud (VPC) and isolated from other AWS networks.
Partition of obligations and job-based access control is innate in the structure of the AWS CloudHSM. AWS screens the wellbeing and network accessibility of your HSMs, however, isn't engaged with the creation and the executives of the key material put away inside your HSMs. You control the HSMs and the age and utilization of your encryption keys.
Use cases
Offload the SSL processing for web servers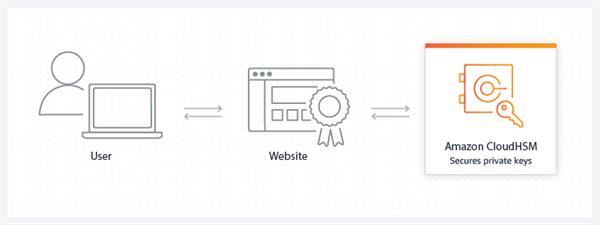
Secure Sockets Layer (SSL) and Transport Layer Security (TLS) are utilized to affirm the personality of web servers and set up secure HTTPS associations over the Internet. You can utilize AWS CloudHSM to offload SSL/TLS handling for your web servers. Utilizing CloudHSM for this handling lessens the weight on your web server and gives additional security by putting away your web server's private key in CloudHSM.
Protect private keys for an issuing certificate authority (CA)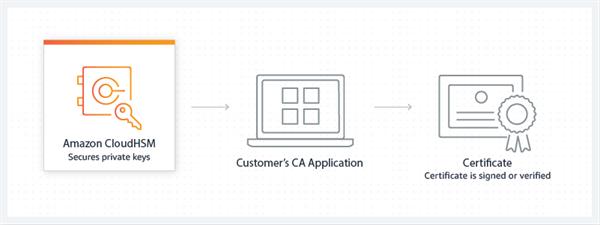
In a public key infrastructure (PKI), a certificate authority (CA) is a confided in substance that issues advanced authentications. These advanced declarations are utilized to recognize an individual or association. You can utilize AWS CloudHSM to store your private keys and sign authentication demands with the goal that you can safely go about as a giving CA to give declarations for your association.
Enable Transparent Data Encryption (TDE) for Oracle databases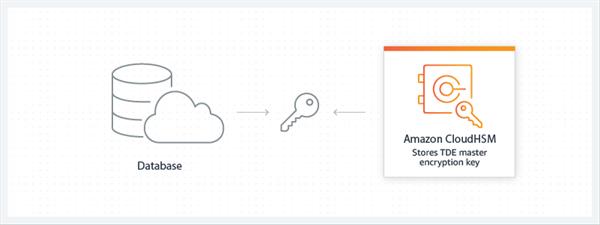
You can utilize AWS CloudHSM to store the Transparent Data Encryption (TDE) ace encryption key for your Oracle database servers that help TDE. Backing for SQL Server is just around the corner. With TDE, upheld database servers can scramble data before putting away it on a circle. If it's not too much trouble note Amazon RDS for Oracle doesn't bolster TDE with CloudHSM; you should utilize AWS Key Management Service for this utilization case.